Okay, quick disclaimer, no crime was committed here. This person agreed to demonstrate how hackers operate as part of a service to keep business owners informed about the type of threats that are out there. This type of attack is happening to someone right now, every day of the week.

This hacker now uses his skills for good. He even worked for the NSA for a time - keeping America safe from foreign threats.
For this particular demonstration, he targeted a business in the service industry...
The Target
The first thing he did was search for a job listing associated with the target business. He quickly found one on a public job listing site. This company was looking for a new account manager.
Armed with the information from the job listing, he performed a simple internet search to find the email of someone in the company's HR department.
Using the wording from the job listing, he filled out a resume template that made him appear to be the ideal candidate for this position. He sent it to Betty@HR with a friendly email reinforcing his amazing skills and eagerness to work for this company.
The Payload
Now here's the nasty catch, the email to Betty@HR included his resume as a .docm attachment.
DOCM files are MS Office Documents for MS Word that contain VBA macros. Basically, it enables a hacker to hide a malicious payload in the background of a seemingly legit document - like a resume.
This is one popular method, but hackers can use all types of phishing techniques and malicious files to gain network access. The attachments can be RTF files, PDF files, PUB files, DOC or DOCX files, XLS files, EXE files - even images and memes.
After reading the email cover letter from this "perfect candidate," how is Betty from HR NOT going to open that file?
Notice: nothing super-high tech has been used by the hacker at this point. That's why hacker schools are able to teach teenagers how to do this so effectively.
The resume file becomes the trojan horse used to carry all sorts of nasty things like password stealers and ransomware.
Living Off the Land
You're probably wondering: 'Won't my antivirus detect this malicious software the moment it executes?' Well, we hope so, however, a number of hackers have discovered ways of executing attacks where they hide behind one of the hundreds of pre-installed tools already on a device that carry out legitimate processes.
Hackers don't even need to write code from scratch, there are plenty of scripts available online that will hide an activity within a systems normal operations - making detection by basic antivirus very difficult.
Hiding malicious activity behind legitimate system tools is known in the cybersecurity world as "Living Off the Land" (or LotL). It's now common practice as most security programs are looking to detect suspicious activity.
Moving Up the Ladder
Betty's click executed the payload that infiltrated the network. From there, the hacker focused on someone in the company who would have access to more damaging information. It was time to steal the CEO's password. The hacker was able to obtain the password in a matter of minutes using a password cracking tool that has been around for years. The CEO's password was way too simple.
Creating a complex password that doesn't contain personal information or references is good security practice. It won't guarantee your password's privacy, but will at least make it harder for bots to crack.
However, even if it took months, this hacker had already breached the network, so he could simply sit back and wait for the right moment to strike. Hackers can use keystroke logging tools installed on your network to decifer the password the next time you use it. The hacker will even get a convenient "alert" on their smartphone or laptop when the password has been captured.
Once the CEO's password was acquired, the boss was "pwnd," the hacker went into his downloads folder and documents folder first to hunt for valuable info by searching for keywords within the file manager. Like most of us, if this CEO had been a little lazy about moving important documents off his device and putting them in a more secure cloud location, the result could have been a huge theft of company funds.
The End Goal
Even if the hacker couldn't access financial docs, the easiest thing for him to do was download ransomeware that bricked the CEO's computer and included a message like this:
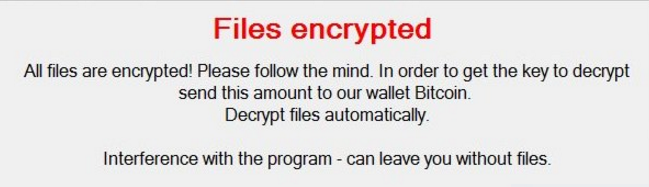
If you get to this point, it's already too late. The Ponemon Institute found that the average ransomware request was around $2,500, however, some enterprises have paid upwards of $50,000 to get their data back.
You never want to find yourself negotiating with a cybercriminal.
What You Can Do to Be More Secure
1) Use updated versions of Office. Most modern Office apps block macros by default.
2) Make sure your users are educated on safe computing. Don't enable macros unless they are 100% sure they know the sender is expecting it. (In our example, there is no reason a resume would have macros enabled.)
3) Use multi-factor authentication to help prevent lateral movement within the network.
4) Use a modern AI based endpoint security solution (like SentinelOne) to help combat modern threats.
5) Make sure you have good backups and have tested them regularly. OneDrive for Business on Windows 10 can now be configured to backup your Desktop, Documents, and Pictures folders. If you have everything backed up in the cloud, you won't have to pay a ransom.
We hope this post was informative. If your business needs a cybersecurity strategy, we'd be happy to help!



