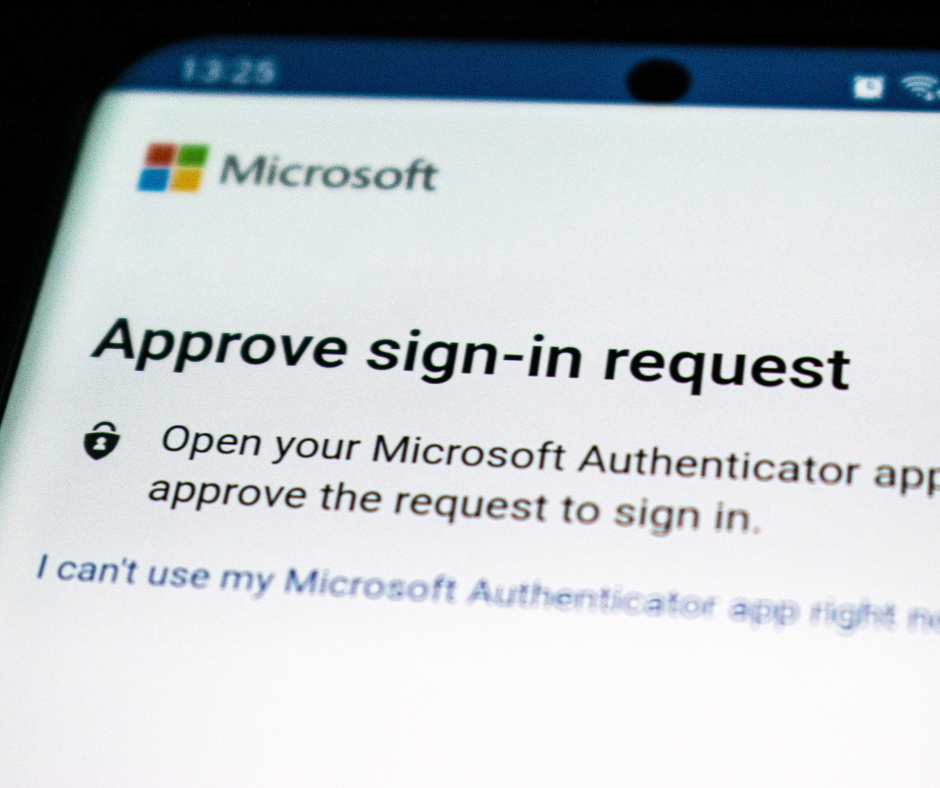
60,000 New Emails! What Happens When Your Inbox Gets Subscription Bombed
Learn all about subscription bombing and what to do if your email becomes compromised in a subscription bomb attack.