
This blog isn’t about fish, fishers, or fishing of any kind. Nor is this about the jam band your brother Spencer followed around for a few years after college. This blog is about one of the most pervasive and surprisingly effective tools that nefarious types use to gain access to your information: Phishing.
Statista posits that 320 billion emails were sent in 2021 and 375 billion are estimated to be sent by 2025. That is 12,000 emails per second, meaning there are a whole bunch of opportunities for phishing to happen.
And it seems, no matter how robust your system and strategy, phishing attempts still find success. Those trying to access your information are getting better at slipping those phishing attacks through the weak spots in platform email defenses. Leaning on a variety of advanced techniques, they're also doing more targeting and research on victims than ever before.
"The end result is always an email that looks genuine to the recipient but looks different to the algorithm that analyzes the content.” says Gil Friedrich, vice president of email security at Avanan.
At this point, we can expect around 1 in 5 phishing attempts to actually get to an inbox. So for this blog, we’re going to examine what happens in the inevitability that one of these emails has been clicked by someone at your organization. Specifically, we’ll look at what phishing really is, how to protect your business from its effects, and when you do click on a malicious link, what next?
What is phishing anyway?
Phishing is defined by Microsoft as an attack that attempts to steal your information, by getting you to reveal personal information like credit card numbers, bank information, or passwords on websites and through links that pretend to be legitimate.
Here are the most common current types of phishing plaguing the internet currently:
|
Business Email Compromise (BEC) |
This specific type of phishing attack uses social engineering, AKA basic human vulnerability, to gain access to sensitive data and your business information. BEC typically targets high-level executives, CEO, or managers in the HR or finance departments as the “best” victims for the risk. |
|
Phishing Emails |
The oldest and original when it comes to stealing info, phishing emails are broadly a type of attack that tricks people into taking an action from emails and messaging services through malicious links or attachments. |
|
Spear Phishing |
Spear phishing is not anything like spearfishing. Instead, a spear phishing situation is very similar to general phishing emails, but instead, these are more advanced and directed at specifically targeted users for specific information that is wanted or needed. Cybercriminals typically impersonate a trusted entity to obtain privileged information or steal money. |
|
Email Bombing |
The most violent-sounding of all phishing attempts, email bombing is a tactic used by cybercriminals when an email account has been compromised already following a data breach. A victim’s inbox will be quickly flooded with an insane number of emails. The real attack will be masked somewhere within those emails, such as confirmation emails for financial transactions using your account, meaning a click that was tricked seems necessary and not obvious. |
How to protect your business.
While admittedly there are phishing attempts that are extremely detailed and are nearly impossible to discern as false. However, implementing regular cyber security training for your employees and adopting a zero-trust policy will provide some major roadblocks for those trying to compromise your business.
Not sure if you need cyber security training? Why You Need to Implement Cyber Security Training Today
So what kinds of suspicious emails should you be looking out for on a daily basis? Here are a handful of real-world examples to always be wary of pulled directly from CISA:
- “We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click the link below, and confirm your identity.”
- “During our regular verification of accounts, we couldn’t verify your information. Please click here to update and verify your information.”
- “Our records indicate that your account was overcharged. You must call us within 7 days to receive your refund.”
If you are ready to start protecting your business from cyber threats, click here
In the following screenshots, use the SLAM method (Sender, Links, Attachments, Message) to see if you can identify why these emails are phishing attempts.
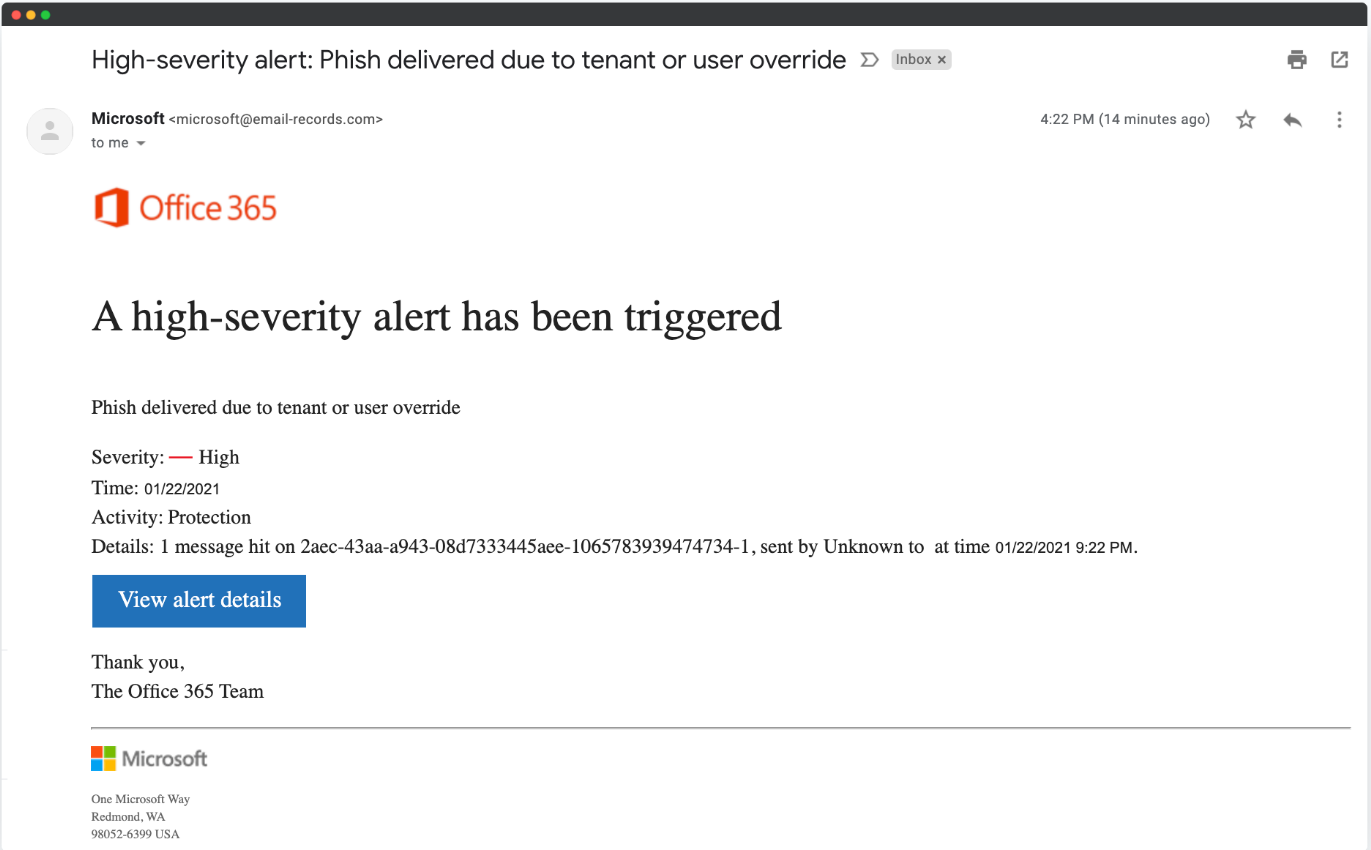
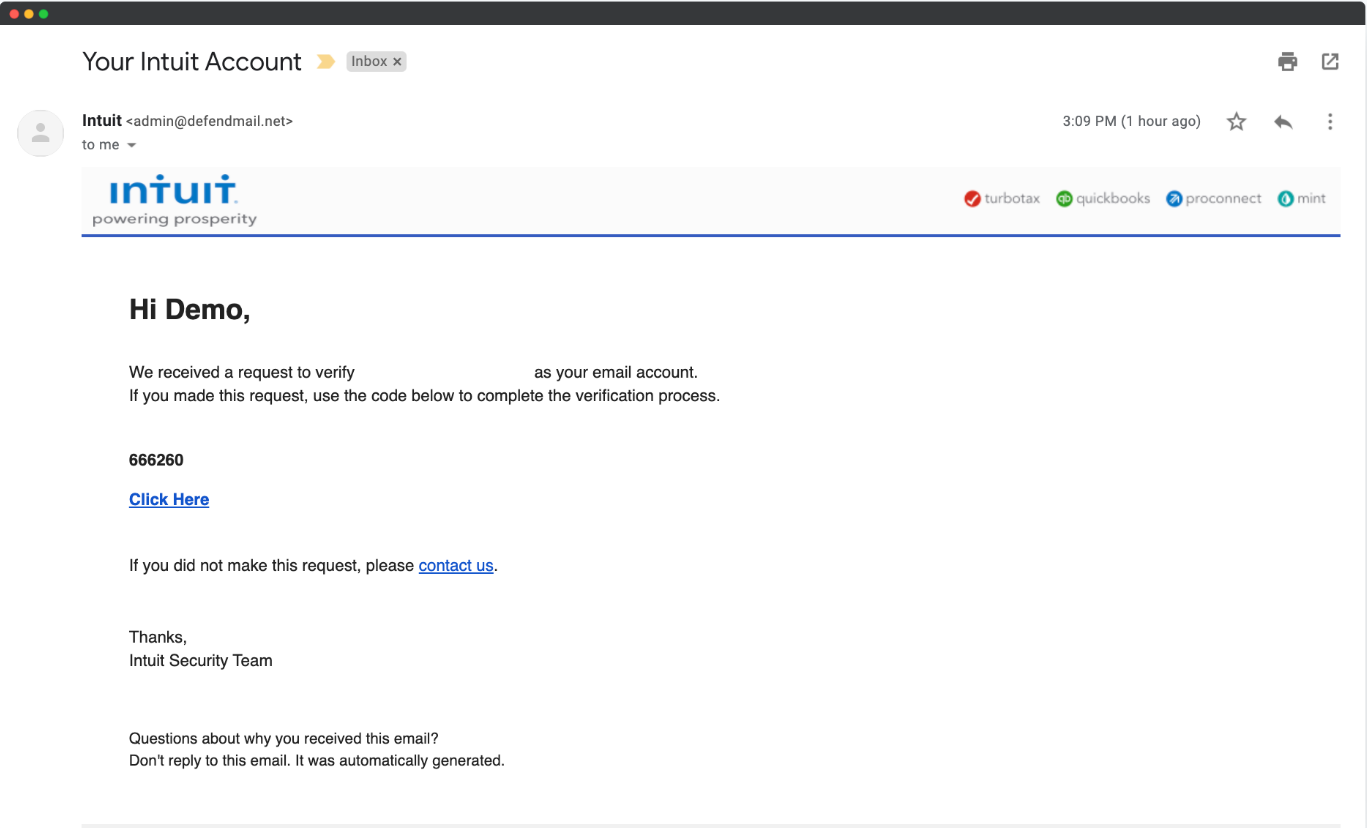
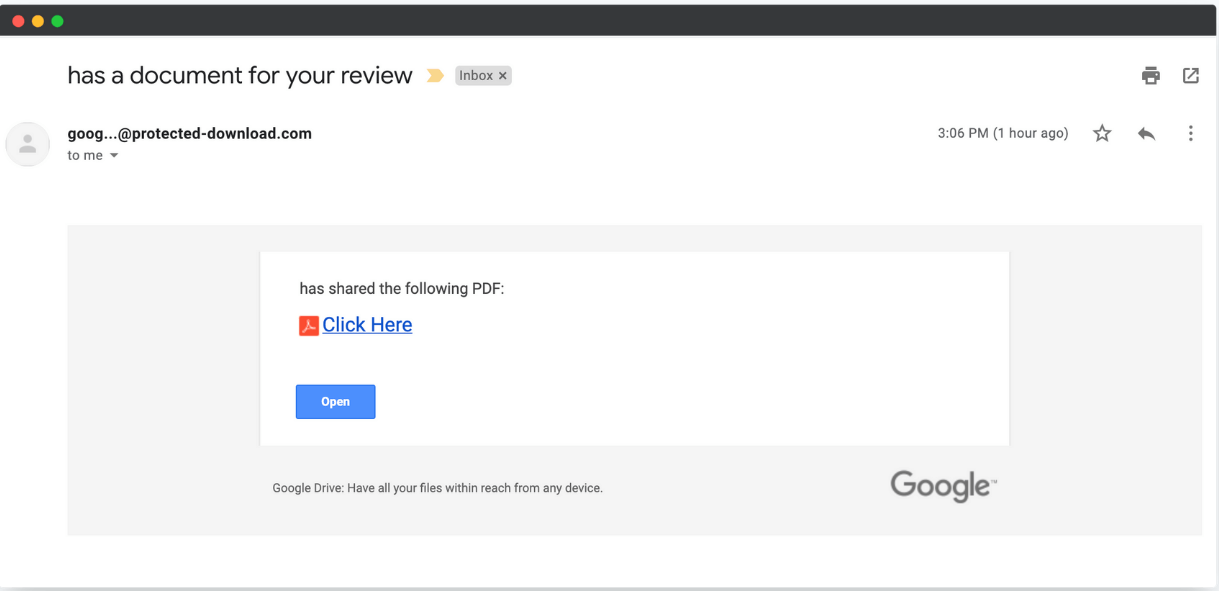
Examples pulled from Hook Security
Knowledge isn’t the only essential tool in our arsenal to fight against phishing. Here is a video from the Cybersecurity and Infrastructure Security Agency on the topic:
So you've been hacked... What next?
We’ve written extensively on the topic, boiling down our advice about what to do after a compromise into five key elements:
- Contact Your Internal IT Department
There's no better alternative than having a dedicated team that has experienced these situations first-hand. Even if you’re simply wary of an odd occurrence on the network or notice something specifically suspicious, contacting your IT team immediately can help prevent further security issues – they’ll know what the most immediate next steps for the network are for your situation. - Change Your Password!
Keeping in mind that 23 million people continue to think "12345" is a solid password, we wanted to share a few thoughts on good password hygiene. Never, ever, ever share your password with someone unless you absolutely must – and even then, never share the password virtually. If you suspect that someone knows your password (or it has been compromised), change it immediately. Changing your password is an easy way to make sure no one else has unauthorized access to your account.
Consider using a password manager: Top 5 Reasons Small Businesses Should Use a Password Manager
- Utilize Two- or Multi-Factor Authorization
Microsoft isn’t shy with their reporting from 2020: 9% of all compromised accounts were not using the multifactor authentication tools available. We can't stress enough just how important Two-factor (2FA) and multifactor authentication (MFA) is for your organization.
Not only do two-factor and multifactor authentication solutions better help prevent theft and unauthorized access, but they also afford your team a higher degree of confidence that only your team is seeing your sensitive and confidential data.
To beef up your security, your multifactor authentication should include at least two different authentication items. Every organization is unique and should choose items from the list that fit the software, and needs, of their day-to-day. Duo, Google, and Microsoft all have applications that leverage MFA your business can use for free. - Check For and Delete Any New Mail Flow Rules
As cyber criminals skulk around your network undetected, they often spend time constructing trap doors that ensure the greatest amount of chaos, when put into action. For instance, when someone compromises an account, they will often create email rules which make it significantly easier for them to cover their tracks, get copies of all your emails, and send out malicious links to others in your organization.
If you’ve been, or feel you’ve been, compromised, be on the lookout for rules like these appearing in your email:- Forwarding copies of every email to an external address.
- Automatically moving emails with a certain keyword to the deleted items.
- Setting up an automatic reply message with a bad link to anyone that emails you.
- Review All of Your Recent Sent & Deleted Emails
Continue on your journey through your email by diving into both your sent and deleted folders to see what the attacker might have sent from your account.
While there are nearly an infinite number of ways criminals can exploit your accounts, many have used compromised accounts to send emails asking clients to pay a bill to a different reception account or to change direct deposit information. If you find messages that fit those criteria, or anything else suspicious, you should follow up with the recipient to let them know what is happening and prevent additional problems.
Conclusion
Leaning on a handful of styles and techniques, cybercriminals around the world are finding success in breaching and manipulating email accounts. Bad actors out to get your information are constantly evolving to slip these attacks through the weak spots in platform email defenses. But with a proactive strategy and a quick response, your team can dramatically mitigate any phishing issues you may experience.
If you need more information on social engineering, phishing, or other general cyber security advice, give us a call at (864) 552-1291 and we'll help you evaluate capabilities and options. Also, sign up for PTG Tech Talk for bi-monthly tech news and consider following us on LinkedIn, Facebook, and Twitter!




